| Home | | | Research | | | Publications | | | | | Developed Courses | | | Seminar | | | Sponsors | | | Links | | | News | | | Contact Us |
Secure Computation LaboratoryProfessor Marten van Dijk |
|
CSE 5095 & ECE 6095: Secure Computation & Storage
| Instructor: Marten van Dijk |
Course Introduction
We discuss various advanced topics in the intersection of cryptography, hardware security, and system security. Depending on the amount of time we will study (1) lattice based cryptography with applications in Fully Homomorphic Encryption (FHE) and Physical Unclonable Functions (PUFs), (2) secure processor architectures in academia such as XOM, Aegis (with memory integrity checking), Ascend with (Oblivious RAM), and Sanctum and in industry e.g. TPM+TXT and Intel SGX, and (3) buffer overflow, privilege separation, capabilities, sandboxing, web security, network security, side channel analysis, user authentication, mobile security, security economics, cyber physical system security, anonymous communication, and database security.Course Requirements:
This is a graduate course and students are expected to have a solid foundation in logical and mathematical reasoning as well as an independent self-motivating attitude to learning and comprehending newly taught concepts (by looking up the necessary papers and chapters to study relevant material).
Course Outcomes:
Students who complete the course will have demonstrated ability to do the following:
- Be able to recall main concepts from lattice based cryptography and its applications to FHE and PUFs. Furthermore, be able to explain mathematical proofs of the underlying theory.
- Be able to explain various aspects of secure processor architecture design.
- Be able to expand on several topics in system security.
- Have obtained a general understanding of cryptography, hardware security, and system security.
- For system security:
http://css.csail.mit.edu/6.858/2014/schedule.html - For lattice based crypto:
https://people.csail.mit.edu/vinodv/6876-Fall2015/index.html
https://www.cims.nyu.edu/~regev/teaching/lattices_fall_2009/ -
For all the lecture videos:
youtube link
In preparation of each lecture you may need to read and study related papers. Reading is an art:
- You will need to give it enough time. Suggested is a maximum of 3-4 hours per paper during which you first read the paper as a newspaper, and next read the paper in more detail. During this process you may want to underline, write out notes, formulate questions, and look-up missing background needed for a more detailed understanding.
- When stuck, just move on and still get the general feeling or gist of what the author tries to communicate.
- After reading, answer for yourself whether you are excited about the material. If not excited, why not? If excited, what exactly interests you?
- In order to gain deeper understanding, look up related work or webpages and try to find an open source demo, or find other applications of the material, or find other resources which help in gaining more understanding.
Course Overview:
- Lattice based crypto: This is very mathematical and computer science oriented. We discuss concepts and proofs. You will be able to understand recent key results; the developments leading to Fully Homomorphic Encryption (FHE) which was a longstanding open problem till 2010 (solved by Craig Gentry) and Silicon Physical Unclonable Functions without non-volatile state which was a 13 year old open problem since its introduction in 2002 (solved by Charles Herder and others).
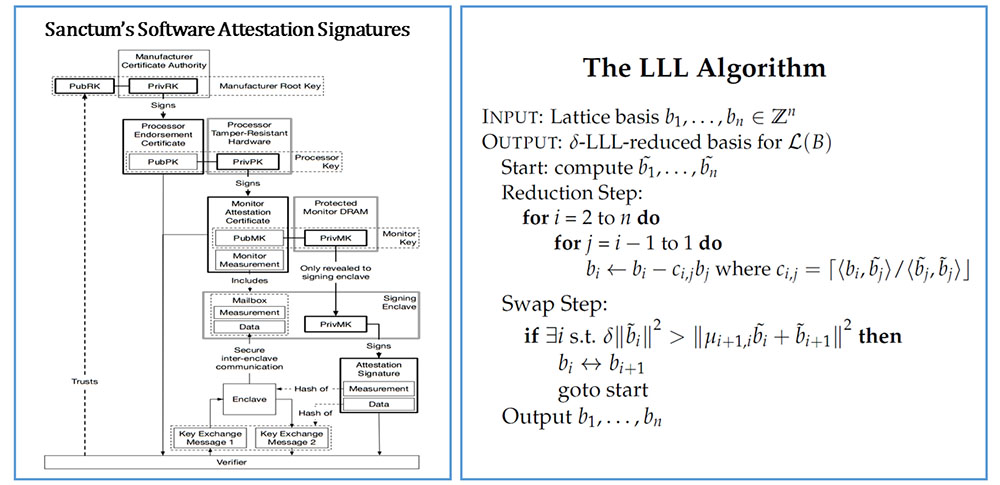
- Secure processor architectures: We will explain memory integrity checking and Oblivious RAM (ORAM) and explain corresponding architectures Aegis and Ascend. We will explain as much as possible of the state-of-the-art industrial secure processor Intel-SGX and its academic simplification called Sanctum (which does not need to be backward compatible).
- System security: Each of you will pick a topic (buffer overflow, privilege separation, capabilities, sandboxing, web security, network security, side channel analysis, user authentication, mobile security, security economics, cyber physical system security, or database security) and prepare a fully detailed slide deck together with an abbreviated side deck to be presented in class. You will also write out a lab (a full directory with source files) which demonstrates the presented material and you will demo your lab in class.
Student's Material
| Week | Date | Topics & Reading Material | Video Lecture |
|---|---|---|---|
| 1 | Jan 25 |
Lattice based crypto: Basis definitions and properties;
Gram-Schmidt orthogonalization; Successive minima; Minkowski’s theorems; Computational problems.
| |
| Feb 1 | cancelled | ||
| Feb 8 | cancelled due to snow, made up Friday April 8 | ||
| Feb 15 | cancelled due to snow, made up Friday April 22 | ||
| 2 | Feb 22 | Lattice based crypto: LLL Algorithm; Learning With Errors (LWE); Hardness of LWE (including average-case worst-case reduction). | |
| 3 | Feb 29 | Lattice based crypto: Secret key and public key encryption from LWE; Fully Homomorphic Encryption (FHE). | |
| 4 | Mar 7 | Lattice based crypto: Fuzzy Extraction; Learning Parities with Noise (LPN) and LPN-based Physical Unclonable Functions (PUFs). | |
| Mar 14 | SPRING BREAK | ||
| 5 | Mar 21 | Catch up on material from previous lectures. | |
| 6 | Mar 28 |
Hardware Security: Memory integrity checking; Encryption; Oblivious RAM (ORAM)
| |
| 7 | Apr 4 | Hardware Security; Secure processor architectures Aegis, Ascend, Intel SGX | |
| Hardware Security; Computer Architecture Background for Intel SGX | |||
| 8 | Apr 8 | Hardware Security; Security Background for Intel SGX | |
| Hardware Security; SGX In-depth Architecture | |||
| 9 | Apr 11 | Hardware Security; SGX Security Analysis | |
| Hardware Security; Sanctum | |||
| 10-12 | Apr 18-25 | Systems Security Presentations | |
| Systems Security Presentations | |||
| Systems Security Presentations | |||
| Systems Security Presentations | |||
| Systems Security Presentations | |||
| May 2 | Finals Week | Finals Week | |
* The course development was partly supported by NSF grant CNS-1413996 for "MACS: A Modular Approach to Cloud Security"
