Secure Processor Architectures
Ascend: A Secure Processor Architecture for Encrypted Computation on Untrusted Programs
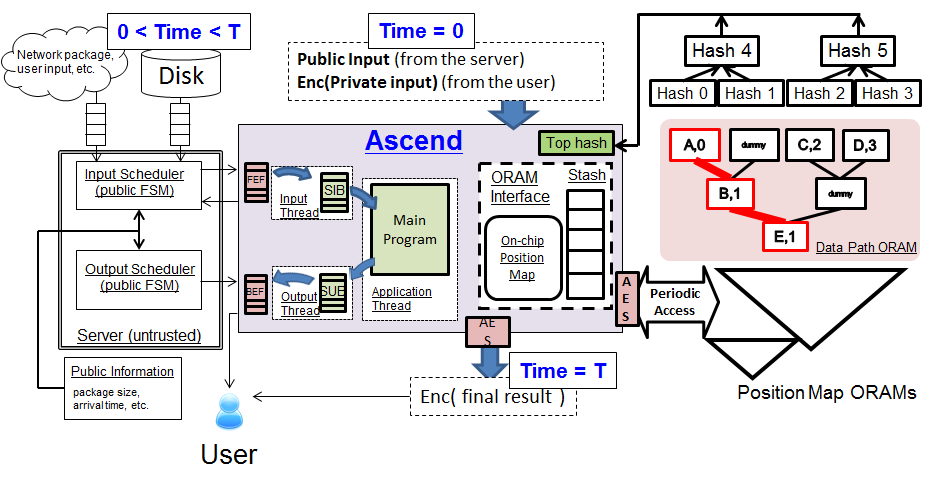
We consider encrypted computation where the user specifies encrypted inputs to an untrusted program, and the server computes on those encrypted inputs. To this end we propose a secure processor architecture, called Ascend, that guarantees privacy of data when arbitrary programs use the data running in a cloud-like environment (e.g., an untrusted server running an untrusted software stack). The key idea to guarantee privacy is obfuscated instruction execution; Ascend does not disclose what instruction is being run at any given time, be it an arithmetic instruction or a memory instruction. Periodic accesses to external instruction and data memory are performed through an Oblivious RAM (ORAM) interface to prevent leakage through memory access patterns. We evaluate the processor architecture on SPEC benchmarks running on encrypted data and quantify overheads.
Ascend started while Marten van Dijk was still working at RSA Laboratories. The list of papers below only include those while at UConn:
- X. Yu, S.K. Haider, L. Ren, C.W. Fletcher, A. Kwon, M. van Dijk, and S. Devadas. "PrORAM: dynamic prefetcher for oblivious RAM", ISCA 2015: 616-628.
- C. Fletcher, L. Ren, A. Kwon, M. van Dijk, E. Stefanov, D. Serpanos, and S. Devadas. "Tiny ORAM: A Low-Latency, Low-Area Hardware ORAM Controller", FCCM 2015.
- C.W. Fletcher, L. Ren, A. Kwon, M. van Dijk, and S. Devadas. "Freecursive ORAM: [Nearly] Free Recursion and Integrity Verification for Position-based Oblivious RAM", ASPLOS 2015: 103-116.
- C.W. Fletcher, L. Ren, X. Yu, M. van Dijk, O. Khan and S. Devadas. "Suppressing the Oblivious RAM timing channel while making information leakage and program efficiency trade-offs", HPCA 2014: 213-224.
- X. Yu, C.W. Fletcher, L. Ren, M. van Dijk and S. Devadas. "Generalized External Interaction with Tamper-Resistant Hardware with Bounded Information Leakage", CCSW'13, 2013.
- L. Ren, C.W. Fletcher, X. Yu, M. van Dijk and S. Devadas. "Integrity Verification for Path Oblivious-RAM", IEEE High Performance Extreme Computing Conference (HPEC) 2013.