Embedded System Security
M-MAP: Multi-Factor Memory Authentication for Secure Embedded Processors
The challenges faced in securing embedded computing systems against multifaceted memory safety vulnerabilities have prompted great interest in the development of memory safety countermeasures. These countermeasures either provide protection only against their corresponding type of vulnerabilities, or incur substantial architectural modifications and overheads in order to provide complete safety, which makes them infeasible for embedded systems.
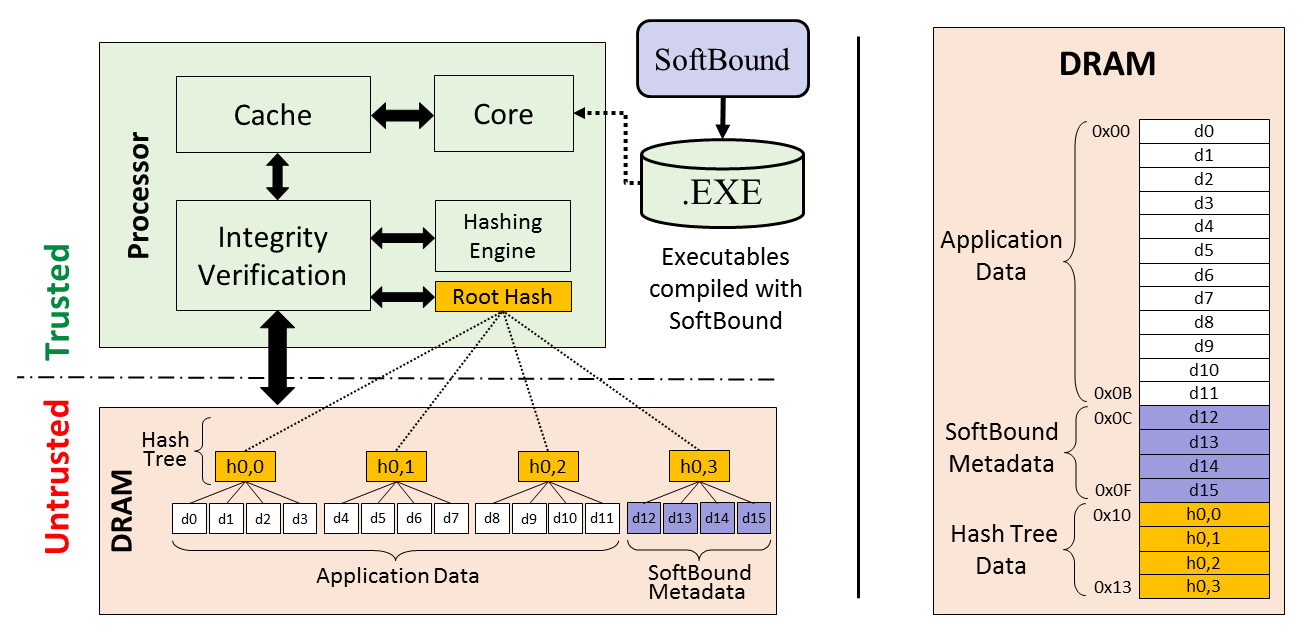
In this project we propose M-MAP: a comprehensive system based on multi-factor memory authentication for complete memory safety. We examine certain crucial implications of composing memory integrity verification and bounds checking schemes in a comprehensive system. Based on these implications, we implement M-MAP with hardware based memory integrity verification and software based bounds checking to achieve a balance between hardware modifications and performance. We demonstrate that M-MAP implemented on top of a lightweight out-of-order processor delivers complete memory safety with only 32% performance overhead on average, while incurring minimal hardware modifications, and area overhead.
Reference
- S. K. Haider, M. Ahmad, F. Hijaz, A. Patni, E. Johnson, M. Seita, O. Khan, M. van Dijk, M-MAP: Multi-Factor Memory Authentication for Secure Embedded Processors, 33rd IEEE Int. Conference on Computer Design, (ICCD), 2015. Link to paper
Exploring the Performance Implications of Memory Safety Primitives in Many-core Processors Executing Multi-threaded Workloads
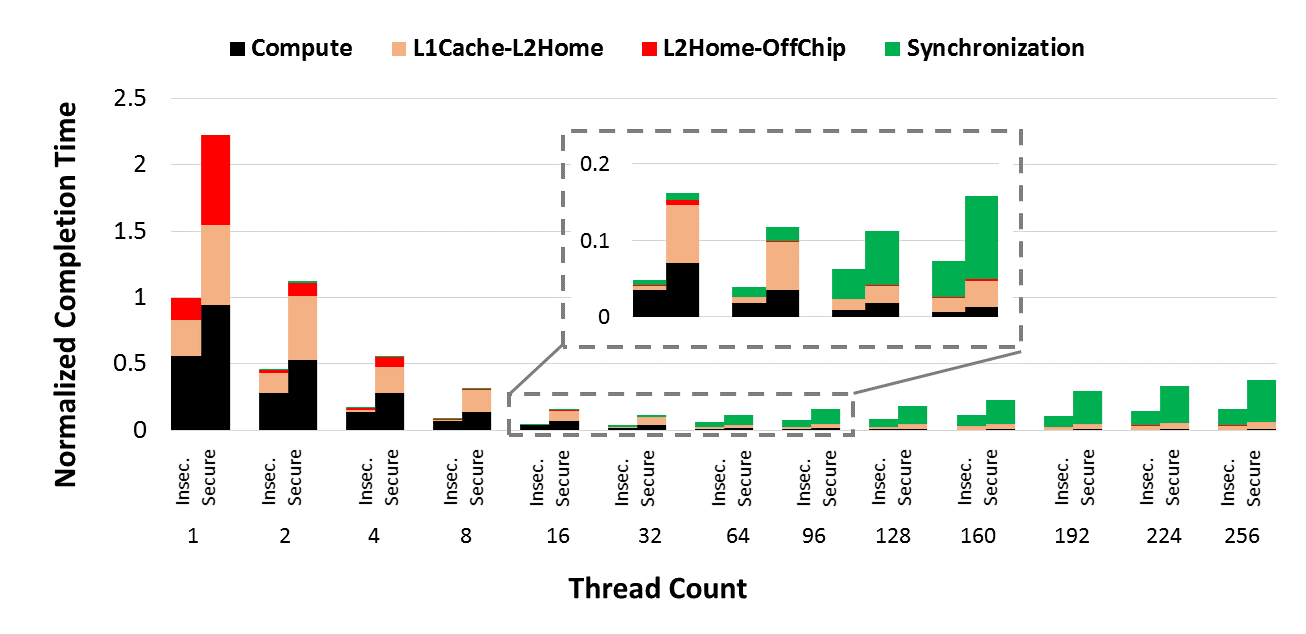
Security is a vital consideration for today’s processor architectures, both at the software and hardware layers. However, security schemes are known to incur significant performance overheads. For example, buffer overflow protection schemes perform software checks for bounds on program data structures, and incur performance overheads that are up to several orders of magnitude. To mitigate these overheads, prior works focus on either changing the security scheme itself, or selectively apply the security scheme to minimize program vulnerabilities. Most of these works also focus primarily on single core processors, with no prior work done in the context of multicore processors. In this paper, we show how increasing thread counts can help hide the latency overheads of security schemes. We also analyze the architectural implications in the context of multicores, and the insights and challenges associated with applying these security schemes on mutithreaded workloads.
Reference
- M. Ahmad, S. K. Haider, F. Hijaz, M. van Dijk, O. Khan, Exploring the Performance Implications of Memory Safety Primitives in Many-core Processors Executing Multi-threaded Workloads, 4th Workshop on Hardware and Architectural Support for Security and Privacy, (HASP), 2015. Link to paper