Supply Chain Management and Counterfeit Detection
Secure and Efficient Authentication and Initialization Protocols for SHIELD
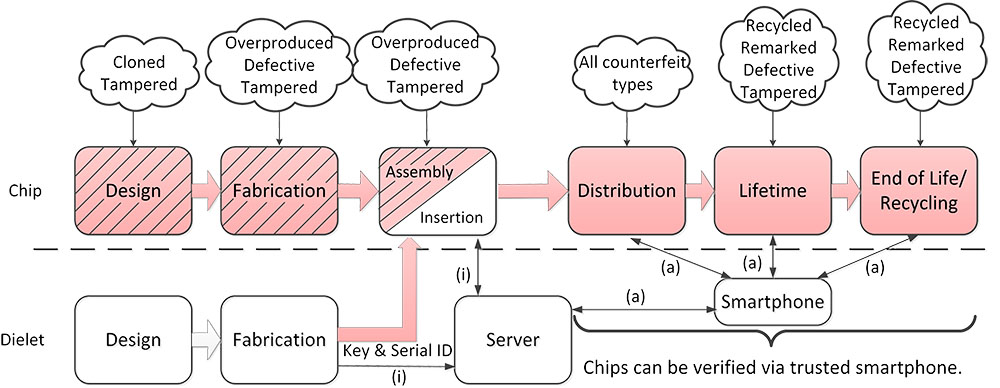
With the globalization of semiconductor production, out-sourcing IC fabrication has become a trend in various aspects. This, however, introduces serious threats from the entire untrusted supply chain. To combat these threats, DARPA (Defense Advanced Research Projects Agency) proposed in 2014 the SHIELD (Supply Chain Hardware Integrity for Electronics Defense) program to design a secure hardware root-of-trust, called dielet, to be inserted into the host package of legitimately produced ICs. Dielets are RF powered and communicate with the outside world through their RF antennas. They have sensors which allow them to passively (without the need for power) record malicious events which can later be read out during an authentication protocol between the dielet and server with a smartphone as intermediary.
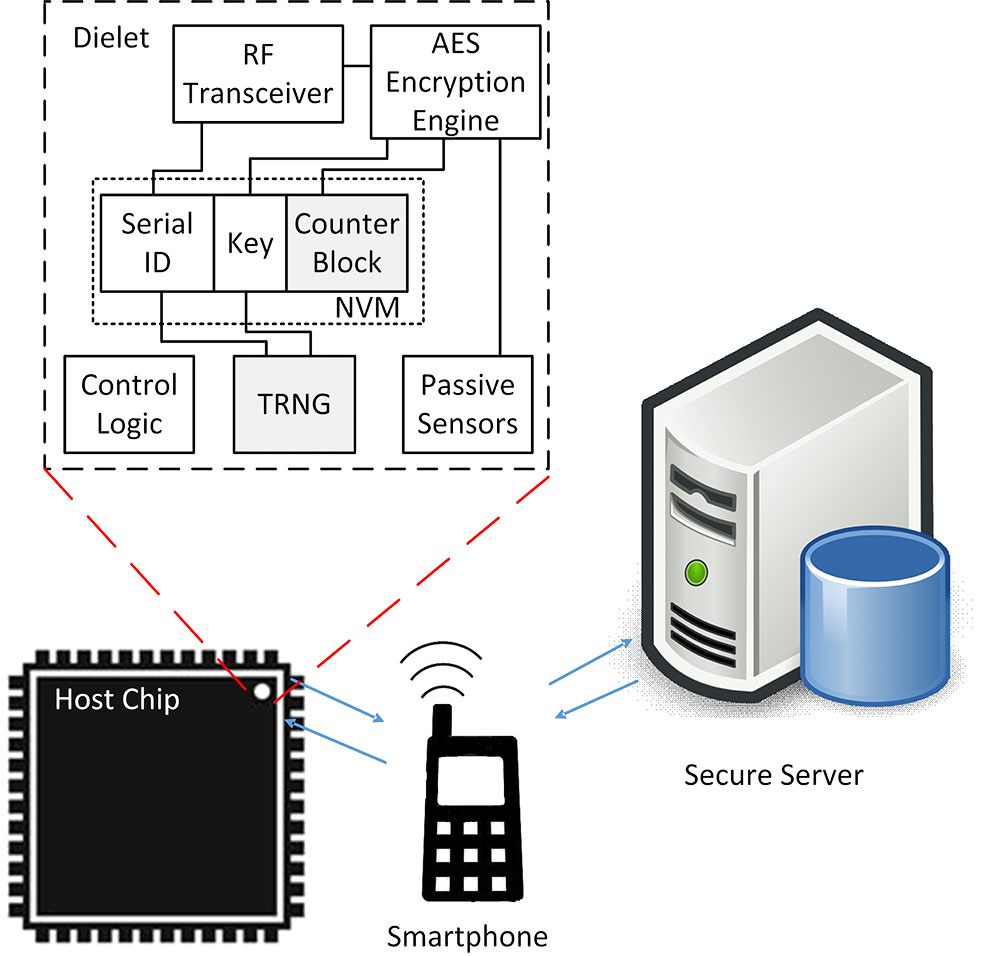
This project introduces a general framework for the initialization and authentication protocols in SHIELD with different adversarial models based on formally-defined security games. We introduce a "try-and-check" attack against DARPA's example authentication protocol in their call for SHIELD proposals which nullifies the effectiveness of SHIELD's main goal of being able to detect and trace adversarial activities with significant probability. We introduce the first concrete initialization protocol and, compared to DARPA's example authentication protocol, introduce an improved authentication protocol which resists the try-and-check attack. The area overhead of our authentication and initialization protocols together is only 64-bit NVM, one 8-bit counter and a TRNG based on a single SRAM-cell together with corresponding control logic. Our findings and rigorous analysis are of utmost importance for the teams which received DARPA's funding for implementing SHIELD.
Reference
- C. Jin and M. van Dijk, "Secure and Efficient Initialization and Authentication Protocols for SHIELD", IACR Cryptology ePrint Archive 2015, 210 (2015). Link to paper
LightSource: Ultra Lightweight Clone Detection of RFID Tags from Sofware Unclonable Responses
Radio-Frequency Identification (RFID) tags have been widely used as a low-cost wireless method for detection of counterfeit product injection in supply chains. In order to adequately perform authentication, current RFID monitoring schemes need to either have a persistent online connection between supply chain partners and the back-end database or have a local database on each partner site. A persistent online connection is not guaranteed and local databases on each partner site impose extra cost and security issues. We introduce a new method in which we use 2-3kb Non-Volatile Memory (NVM) in RFID tags themselves to function as a very small "encoded local database". Our method allows us to get rid of local databases and there is no need to have any connection between supply chain partners and the back-end database except when they want to verify products.
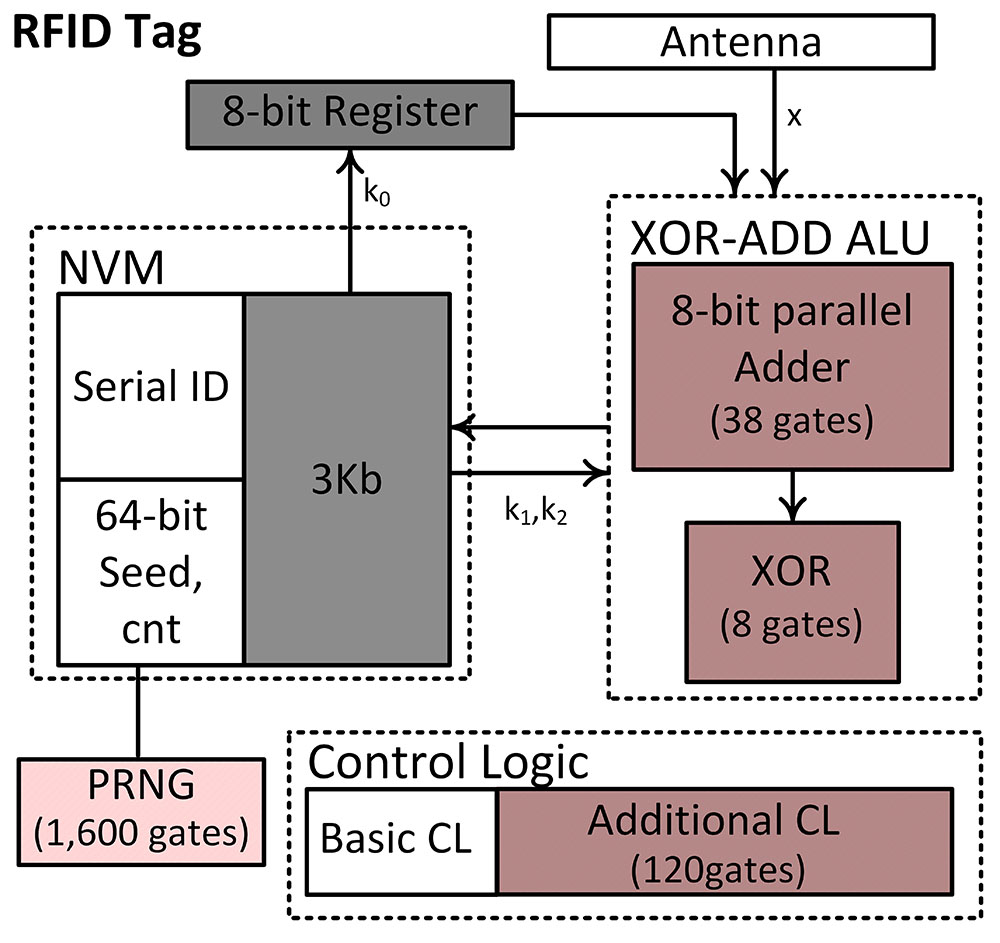
We formally define black-box software unclonability and prove our scheme to satisfy this property. To this purpose we introduce a simple "XOR-ADD" function and prove it is hard to predict its challenge-response behavior if given only one challenge response pair. The XOR-ADD function with control logic can be implemented using at most 170 gates. This implies that our scheme is compatible with the strict power consumption constraints of cheap EPC Class 1 Gen 2 RFIDs.
Reference
- H. Maleki, R. Rahaeimehr and M. van Dijk, "LightSource: Ultra Lightweight Clone Detection of RFID Tags from Software Unclonable Responses", IACR Cryptology ePrint Archive 2016, 608 (2016). Link to paper