Hardware Trojan Design and Detection
Optimized for area and performance, IP cores are essential elements of design reuse in the electronic design automation (EDA) industry; modern electronic systems increasingly use third party IP cores as their basic building blocks. In order to protect intellectual property, these third party IP cores are generally offered as gate-level netlists which are Boolean function representations of the cores’ logics. This state of affairs leads to a pressing security challenge: if one cannot ascertain whether a third party IP core is based on a trusted source code and has been generated using a trusted toolchain, how can one prevent attacks by a malicious logic, also called a hardware trojan, embedded inside the IP core resulting in data leakage or harm to the normal functionality of the IP core once activated? This project seeks to develop the first formal framework of hardware trojan design and detection based on a new rigorous classification of hardware Trojans, see link for details and preliminary results.
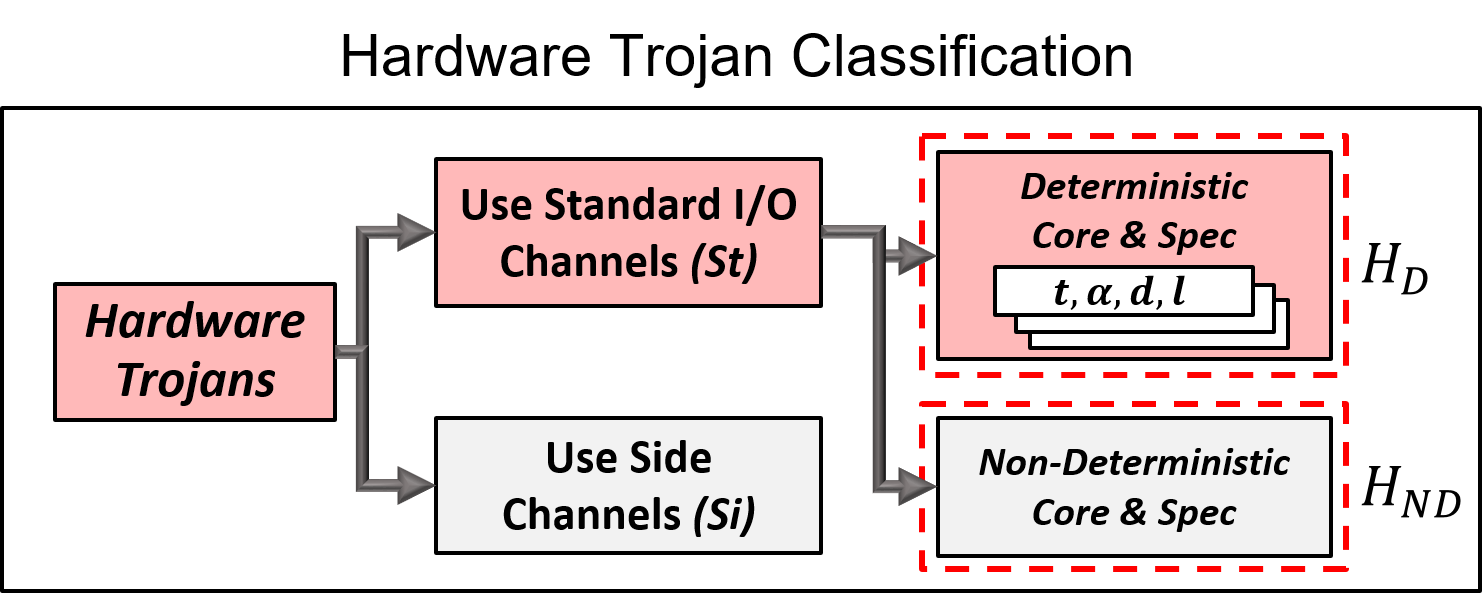
The formal framework allows on one hand a deep understanding of the hardware trojan design space leading to the understanding that current benchmarked Trojans are the ones that are the easiest to detect and therefore only reflect the tip of the iceberg. On the other hand the framework gives guidance to how to detect complex trojans: during a learning phase the IP core goes through functional testing, which leads to a blacklist of wire combinations used to track suspicious behavior by logic added to the IP core during a tagging phase.
The projects involves the development of HaTCh, a new rigorous framework which differentiates Trojans with respect to their activation mechanism, payload channels, determinism of the IP core, and payload functionality. HaTCh characterizes (1) the class of Trojans that can possibly be detected with negligible false negative rate; Trojans outside this class are vulnerable to exploits over covert channels. Given this class, HaTCh defines (2) a hierarchy of Trojans based on the width of their trigger signal, the latency between trigger condition and malicious payload, and their probability of exhibiting implicit malicious behavior. This reveals (3) the (fearfully large) trojan design landscape. The proposed HaTCh tool (4) detects complex Trojans from this landscape using a learning phase and tagging phase. It offers (5) negligible false negative rates, (6) small controllable false positive rates, (7) a reasonable area overhead of the tagging circuitry, and (8) a learning phase with practical runtime if certain trojan properties/invariants (such as locality of wires) can be used.
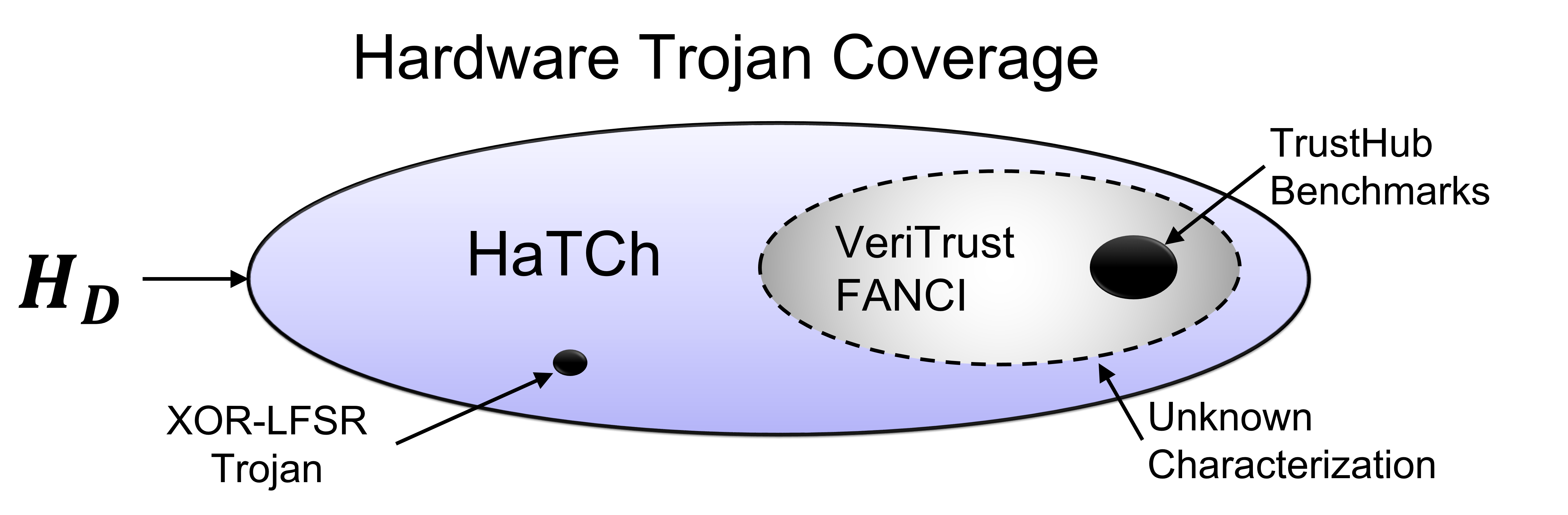
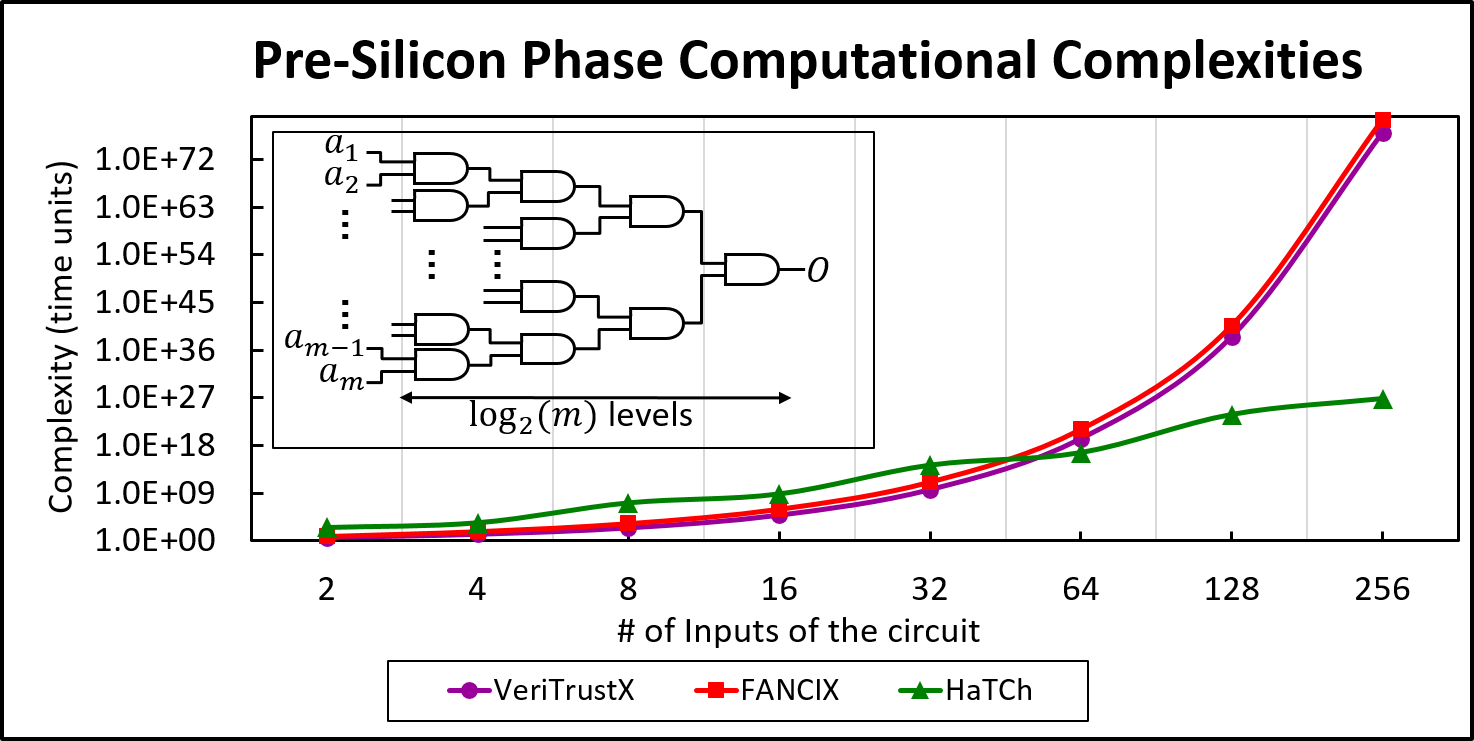
HaTCh offers complete coverage and transparent detection guarantees for a large class of deterministic hardware Trojans. The figure above compares the coverages offered by different Trojan detection schemes. Although VeriTrust and FANCI can detect publicly known TrustHub Trojans, it is unclear what security guarantees they offer outside TrustHub. On the other hand, HaTCh is capable of detecting any Trojan from the deterministic class of Trojans, whether the Trojan is publicly known or unknown, with negligible false negative rate and a controllable false positive rate. The following figure shows computational complexities of different countermeasures against the number of inputs of a m-input AND gate. HaTCh offers orders of magnitude lower complexity compared to the other schemes, particularly for circuits with more than 64 inputs.
This is ongoing collaborative work with S. K. Haider, C. Jin, M. Ahmad, S. M. Devu, O. Khan, and M. van Dijk. A preliminary eprint (showing an evolution of several versions) explains the above ideas and can be found here.
References
- S.K. Haider, C. Jin, and M. van Dijk, “Advancing the State-of-the-Art in Hardware Trojans Design”, arXiv:1605.08413, 2016. Link to paper
- S.K. Haider, C. Jin, M. Ahmad, D.M. Shila, O. Khan, M. van Dijk, "Advancing the State-of-the-Art in Hardware Trojans Detection", Cryptology ePrint Archive, Report 2014/943, 2014. Link to paper